Backscatters are still active NDR’s who will be delivered to companies where after some investigation the mail is never send from. There are a few possibilities to prevent this, one of this is with SPF records.</p>
I went for some further investigation on how to block those irritating mails. I found out that it could be done with Transport Rules in Exchange 2007.
In this tutorial I will explain how you can configure to get rid of the irritating backscatters.
First we will create a transport rule which adds a tag to the header of an e-mail. With this we can recognize e-mails which are send from our own server.
We can do this by opening the EMC and go to the Hub Transport Server via the Organizational Configuration. After that we can open the tab Transport Rules.
Next step is selecting the option to create a new Transport Rule in the right menu.
In this case we choose the following name Add tag to header but this can be any name you like. When you've choosen the name you like you will click on next
On the next page we will select which conditions the mail must met before we will apply the transport rule
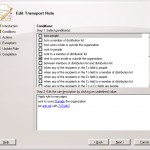
Here we define that we want to apply the rule on every mail that is send to outside via the Hub Transport server. When this has been defined we click on next
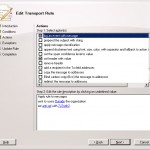
Next step is the action that needs to be executed. As I said earlier we want to add something to the header of the mail. We can do this by selecting the option set header with value. This rule will be added to the lower part of the screen. The only thing we need to specify is the values we want to add.
First we will define the tag itself
We will give the tag the name anti-spf , this is a name you can change if you like, remember it because we will need it later on. Next we need to specify the value that we want to give to the tag. The best option is to give it a random value. This makes it a little bit harder to hack, but it's still possible because it's a static value
When both values are defined we will click on next
We will get a short summary en we can click on next to continue. When the rule is created succesfully we will get the screen below
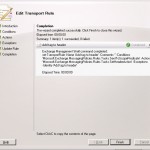
Each mail who is send to the outside world will get an extra tag in the header anti-spf: 7uTreth2
The next step is to create a Transport Rule who checks if the NDR mail contains the tag.
To do this we will select the option to create a new Transport Rule in the right menu
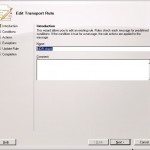
We will give it a name, in this case NDR Check, and click on next
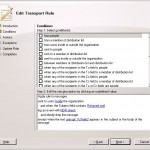
The next step is to define the conditions the mail must met before we will apply the Transport Rule. In this case we chec:
- if the mail is send to internal (sent to users inside your organization)
- if the subjected contains Returned mail (Subject field contains specific words)
When selecting the option Subject field contains don't forget to add the value Returned mail manually.
The next step is to define the action that needs to be executed
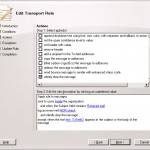
In this case we define that
- an item should be logged in the event log with the text NDR Check
- the mail should not be delivered
It can be that the action drop the message is OK for you, in this case you only need to select this one. When you are satisfied with the settings click on next.
The last step is to define the exceptions, if we don't do it all mails to internal users with the text Returned mail will be dropped. This is not what we want because this would cause legal NDR's also to be dropped.
By checking the body of the mail for the text anti-spf: 7uTreth2 we can prevent that legal NDR's will be blocked.
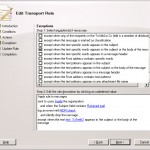
When this is defined we click on next en the rule will be created. When the rule is created succesfully you will get the screen below
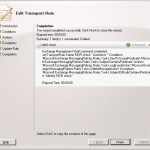
I must admit that it will cost you some time to create the rules but it wil save you a lot of calls from users with questions about NDR's.